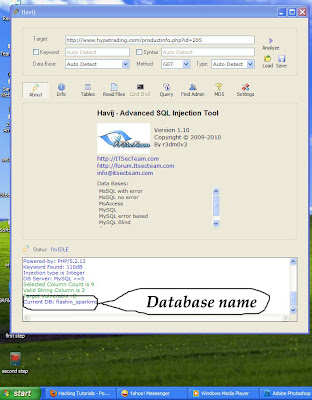
Google is a treasure trove full of important information, especially for
the underground world. This Potential fact can also be utilized in the
data for the username and password stored on a server.
If the administrator save important data not in the complete system authentication folder, then most likely be reached by the google search engine. If data is successfully steal in by the unauthorized person, then the will be in misuse.
Here, some google search syntax to crawl the password:
1. "Login: *" "password =*" filetype: xls (searching data command to the system files that are stored in Microsoft Excel)
2. allinurl: auth_user_file.txt (to find files auth_user_file.txt containing password on server).
3. filetype: xls inurl: "password.xls" (looking for username and password in ms excel format). This command can change with admin.xls)
4. intitle: login password (get link to the login page with the login words on the title and password words anywhere. If you want to the query index more pages, type allintitle)
5. intitle: "Index of" master.passwd (index the master password page)
6. index of / backup (will search the index backup file on server)
7. intitle: index.of people.lst (will find web pages that contain user list).
8. intitle: index.of passwd.bak ( will search the index backup password files)
9. intitle: "Index of" pwd.db (searching database password files).
10. intitle: "Index of .. etc" passwd (this command will index the password sequence page).
11. index.of passlist.txt (will load the page containing password list in the clear text format).
12. index.of.secret (google will bring on the page contains confidential document). This syntax also changed with government query site: gov to search for government secret files, including password data) or use syntax: index.of.private
13. filetype: xls username password email (will find spreadsheets filese containing a list of username and password).
14. "# PhpMyAdmin MySQL-Dump" filetype: txt (will index the page containing sensitive data administration that build with php)
15. inurl: ipsec.secrets-history-bugs (contains confidential data that have only by the super user). or order with inurl: ipsec.secrets "holds shared secrets"
16. inurl: ipsec.conf-intitle: manpage (useful to find files containing important data for hacking)
17. inurl: "wvdial.conf" intext: "password" (display the dialup connection that contain phone number, username and password)
18. inurl: "user.xls" intext: "password" (showing url that save username and passwords in spread sheet files)
19. filetype: ldb admin (web server will look for the store password in a database that dos not delete by googledork)
20.inurl: search / admin.php (will look for php web page for admin login). If you are lucky, you will find admin configuration page to create a new user.
21. inurl: password.log filetype:log (this keyword is to search for log files in a specific url)
22. filetype: reg HKEY_CURRENT_USER username (this keyword used to look for reg files (registyry) to the path HCU (Hkey_Current_User))
Here, some of the other syntax google that we need to look for confidential data :
"Http://username: password @ www ..." filetype: bak inurl: "htaccess | passwd | shadow | ht users"
(this command is to take the user names and passwords for backup files)
filetype:mdb inurl:”account|users|admin|administrators|passwd|password” mdb files (this command is to take the password information)
filetype:ini ws_ftp pwd (searching admin password with ws_ftp.ini file)
intitle: "Index of" pwd.db (searching the encrypted usernames and passwords)
inurl:admin inurl:backup intitle:index.of (searching directories whose names contain the words admin and backup)
“Index of/” “Parent Directory” “WS _ FTP.ini” filetype:ini WS _ FTP PWD (WS_FTP configuration files is to take FTP server access passwords)
ext:pwd inurl:(service|authors|administrators|users) “# -FrontPage-” (there is Microsoft FrontPage passwords)
filetype: sql ( "passwd values ****" |" password values ****" | "pass values ****") searching a SQL code and passwords stored in the database)
intitle:index.of trillian.ini (configuration files for the Trillian IM)
eggdrop filetype:user (user configuration files for the Eggdrop ircbot)
filetype:conf slapd.conf (configuration files for OpenLDAP)
inurl:”wvdial.conf” intext:”password” (configuration files for WV Dial)
ext:ini eudora.ini (configuration files for the Eudora mail client)
filetype: mdb inurl: users.mdb (potentially to take user account information with Microsoft Access files)
intext:”powered by Web Wiz Journal” (websites using Web Wiz Journal, which in its standard configuration allows access to the passwords file – just enter http:///journal/journal.mdb instead of the default http:///journal/)
“Powered by DUclassified” -site:duware.com "Powered by DUclassified"-site: duware.com
“Powered by DUcalendar” -site:duware.com "Powered by DUcalendar"-site: duware.com
“Powered by DUdirectory” -site:duware.com "Powered by DUdirectory"-site: duware.com
“Powered by DUclassmate” -site:duware.com "Powered by DUclassmate"-site: duware.com
“Powered by DUdownload” -site:duware.com "Powered by DUdownload"-site: duware.com
“Powered by DUpaypal” -site:duware.com "Powered by DUpaypal"-site: duware.com
“Powered by DUforum” -site:duware.com "Powered by DUforum"-site: duware.com
intitle:dupics inurl:(add.asp | default.asp |view.asp | voting.asp) -site:duware.com (websites that use DUclassified, DUcalendar, DUdirectory, DUclassmate, DUdownload, DUpaypal, DUforum or DUpics applications, by default allows us to retrieve passwords file)
To DUclassified, just visit http:///duClassified/ _private / duclassified.mdb
or http:///duClassified/ or http:///duClassified/
intext: "BiTBOARD v2.0" "BiTSHiFTERS Bulletin Board" (Bitboard2 use the website bulletin board, the default settings make it possible to retrieve the passwords files to be obtained with the ways http:///forum/admin/data _ passwd.dat
or http:///forum/forum.php) or http:///forum/forum.php)
Searching for specific documents :
filetype: xls inurl: "email.xls" (potentially to take the information contact)
“phone * * *” “address *” “e-mail” intitle:”curriculum vitae”
CVs "not for distribution" (confidential documents containing the confidential clause
buddylist.blt)
AIM contacts list AIM contacts list
intitle:index.of mystuff.xml intitle: index.of mystuff.xml
Trillian IM contacts list Trillian IM contacts list
filetype:ctt “msn” filetype: Note "msn"
MSN contacts list MSN contacts list
filetype:QDF (QDF database files for the Quicken financial application)
intitle: index.of finances.xls (finances.xls files, potentially to take information on bank accounts, financial Summaries and credit card numbers)
intitle: "Index Of"-inurl: maillog (potentially to retrieve e-mail account)
Our Partner Site:
Visit https://www.faadoocoupons.com
If the administrator save important data not in the complete system authentication folder, then most likely be reached by the google search engine. If data is successfully steal in by the unauthorized person, then the will be in misuse.
Here, some google search syntax to crawl the password:
1. "Login: *" "password =*" filetype: xls (searching data command to the system files that are stored in Microsoft Excel)
2. allinurl: auth_user_file.txt (to find files auth_user_file.txt containing password on server).
3. filetype: xls inurl: "password.xls" (looking for username and password in ms excel format). This command can change with admin.xls)
4. intitle: login password (get link to the login page with the login words on the title and password words anywhere. If you want to the query index more pages, type allintitle)
5. intitle: "Index of" master.passwd (index the master password page)
6. index of / backup (will search the index backup file on server)
7. intitle: index.of people.lst (will find web pages that contain user list).
8. intitle: index.of passwd.bak ( will search the index backup password files)
9. intitle: "Index of" pwd.db (searching database password files).
10. intitle: "Index of .. etc" passwd (this command will index the password sequence page).
11. index.of passlist.txt (will load the page containing password list in the clear text format).
12. index.of.secret (google will bring on the page contains confidential document). This syntax also changed with government query site: gov to search for government secret files, including password data) or use syntax: index.of.private
13. filetype: xls username password email (will find spreadsheets filese containing a list of username and password).
14. "# PhpMyAdmin MySQL-Dump" filetype: txt (will index the page containing sensitive data administration that build with php)
15. inurl: ipsec.secrets-history-bugs (contains confidential data that have only by the super user). or order with inurl: ipsec.secrets "holds shared secrets"
16. inurl: ipsec.conf-intitle: manpage (useful to find files containing important data for hacking)
17. inurl: "wvdial.conf" intext: "password" (display the dialup connection that contain phone number, username and password)
18. inurl: "user.xls" intext: "password" (showing url that save username and passwords in spread sheet files)
19. filetype: ldb admin (web server will look for the store password in a database that dos not delete by googledork)
20.inurl: search / admin.php (will look for php web page for admin login). If you are lucky, you will find admin configuration page to create a new user.
21. inurl: password.log filetype:log (this keyword is to search for log files in a specific url)
22. filetype: reg HKEY_CURRENT_USER username (this keyword used to look for reg files (registyry) to the path HCU (Hkey_Current_User))
Here, some of the other syntax google that we need to look for confidential data :
"Http://username: password @ www ..." filetype: bak inurl: "htaccess | passwd | shadow | ht users"
(this command is to take the user names and passwords for backup files)
filetype:mdb inurl:”account|users|admin|administrators|passwd|password” mdb files (this command is to take the password information)
filetype:ini ws_ftp pwd (searching admin password with ws_ftp.ini file)
intitle: "Index of" pwd.db (searching the encrypted usernames and passwords)
inurl:admin inurl:backup intitle:index.of (searching directories whose names contain the words admin and backup)
“Index of/” “Parent Directory” “WS _ FTP.ini” filetype:ini WS _ FTP PWD (WS_FTP configuration files is to take FTP server access passwords)
ext:pwd inurl:(service|authors|administrators|users) “# -FrontPage-” (there is Microsoft FrontPage passwords)
filetype: sql ( "passwd values ****" |" password values ****" | "pass values ****") searching a SQL code and passwords stored in the database)
intitle:index.of trillian.ini (configuration files for the Trillian IM)
eggdrop filetype:user (user configuration files for the Eggdrop ircbot)
filetype:conf slapd.conf (configuration files for OpenLDAP)
inurl:”wvdial.conf” intext:”password” (configuration files for WV Dial)
ext:ini eudora.ini (configuration files for the Eudora mail client)
filetype: mdb inurl: users.mdb (potentially to take user account information with Microsoft Access files)
intext:”powered by Web Wiz Journal” (websites using Web Wiz Journal, which in its standard configuration allows access to the passwords file – just enter http:///journal/journal.mdb instead of the default http:///journal/)
“Powered by DUclassified” -site:duware.com "Powered by DUclassified"-site: duware.com
“Powered by DUcalendar” -site:duware.com "Powered by DUcalendar"-site: duware.com
“Powered by DUdirectory” -site:duware.com "Powered by DUdirectory"-site: duware.com
“Powered by DUclassmate” -site:duware.com "Powered by DUclassmate"-site: duware.com
“Powered by DUdownload” -site:duware.com "Powered by DUdownload"-site: duware.com
“Powered by DUpaypal” -site:duware.com "Powered by DUpaypal"-site: duware.com
“Powered by DUforum” -site:duware.com "Powered by DUforum"-site: duware.com
intitle:dupics inurl:(add.asp | default.asp |view.asp | voting.asp) -site:duware.com (websites that use DUclassified, DUcalendar, DUdirectory, DUclassmate, DUdownload, DUpaypal, DUforum or DUpics applications, by default allows us to retrieve passwords file)
To DUclassified, just visit http:///duClassified/ _private / duclassified.mdb
or http:///duClassified/ or http:///duClassified/
intext: "BiTBOARD v2.0" "BiTSHiFTERS Bulletin Board" (Bitboard2 use the website bulletin board, the default settings make it possible to retrieve the passwords files to be obtained with the ways http:///forum/admin/data _ passwd.dat
or http:///forum/forum.php) or http:///forum/forum.php)
Searching for specific documents :
filetype: xls inurl: "email.xls" (potentially to take the information contact)
“phone * * *” “address *” “e-mail” intitle:”curriculum vitae”
CVs "not for distribution" (confidential documents containing the confidential clause
buddylist.blt)
AIM contacts list AIM contacts list
intitle:index.of mystuff.xml intitle: index.of mystuff.xml
Trillian IM contacts list Trillian IM contacts list
filetype:ctt “msn” filetype: Note "msn"
MSN contacts list MSN contacts list
filetype:QDF (QDF database files for the Quicken financial application)
intitle: index.of finances.xls (finances.xls files, potentially to take information on bank accounts, financial Summaries and credit card numbers)
intitle: "Index Of"-inurl: maillog (potentially to retrieve e-mail account)
Our Partner Site:
Visit https://www.faadoocoupons.com



Tutorial+by+Hackw0rm.png)
Tutorial+by+Hackw0rm.png)
Tutorial+by+Hackw0rm.png)
Tutorial+by+Hackw0rm.png)
Tutorial+by+Hackw0rm.png)
Tutorial+by+Hackw0rm.png)